How does Altoo protect confidential customer data? Summer 2020, Stefan Thiel, CTO Altoo AG
At Altoo, we help wealthy private individuals to keep track and control of their assets. With a larger amount of wealth comes complexity: Our customers have multiple e-banking relationships. They have investments in real estate, private equity, and collectibles. Dealing with so many service providers is not easy. It is even more complex and difficult to keep the overview and gain transparency over all assets.
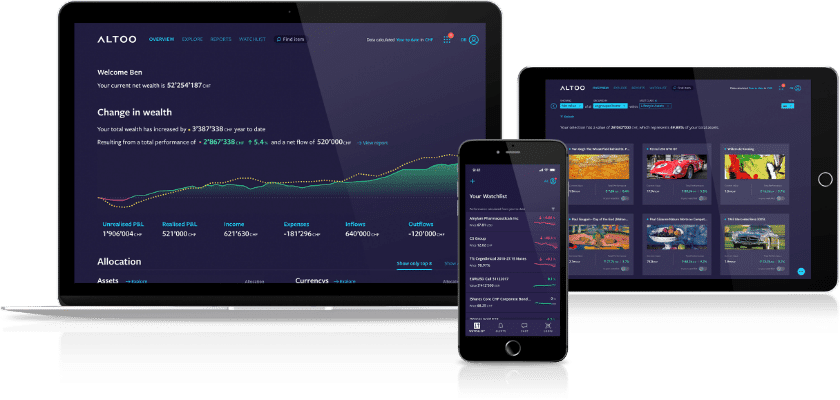
The Altoo Wealth Platform is a ‘Software as a Service’ that provides simplicity and control for such diverse assets by connecting wealth, people and processes in a very intuitive and simple way. In addition, it allows individuals and their families to consolidate, interact and communicate with their wealth data securely. With a strong focus on security, Altoo’s technology is developed and hosted in Switzerland.
Protecting stored confidential customer data
Altoo has a particular responsibility as our customers trust us with all of their private wealth data. Therefore, providing very high information security is a key strategic priority of the Altoo Wealth Platform. We continuously invest in improving our platform’s security to ensure confidentiality, integrity and availability of our customers’ data. In this blog we focus specifically on encryption of confidential data.
Encryption of stored confidential customer data
From a security perspective we want confidential data to be encrypted to protect it from physical and cyber threats. There are several approaches to do so:
Wealth Aggregation: Simple, Dynamic, and Secure Beyond Compare. Discover the Altoo Wealth Platform!
- file system encryption,
- database encryption,
- application level encryption
Let us follow some of our thoughts when designing our encryption approach.
Data protection laws require us to support customer requests to delete their data. As we want data to be replicated multiple times across our private cloud to guarantee availability and uptime on any server’s failure, such a data deletion needs to find and delete all copies of that data. Using a cryptographic trick, we can just delete the keys that are needed to access that data. It makes all copies, wherever stored, inaccessible at the same time.
Protecting data from malicious activities is another goal. This goal cannot be achieved using file system or database encryption as operational staff cannot be prevented from accessing that data.
Our architecture, applying Event Source (see White Paper about the Altoo Wealth Platform architecture), allows us to encrypt within the storage access layer. From an operations perspective, this is considered an application level encryption, whereas application developers perceive it as a storage layer feature similar to a database level encryption, which is transparent to them. It allows to use different keys for each data entity and prevents access to stored confidential data on system level.
Protecting stored data
Stored data faces multiple threats. It needs physical protection to prevent being carried away with the hardware it is stored on. And it needs cyber protection to control electronic access. For both, we use the principle of onion-like layers of protection. Starting from the outside the most important layers are:
Physical space protection
Cyberspace protection
Swiss-based data centre
We operate our own hardware in a secure Tier Level 4 data centre in Switzerland. Level 4 is the highest level certification of data centres according to an US standard (TIA-942) about security and availability of a data centre’s services.
Outer firewalls
At the outer boundary of our private cloud we engage a high availability stack of firewalls to fight brute force attacks and inspect the legitimate traffic we have to let through into our DMZ for servicing our customers.
Secure key stores guarding the encryption keys
To protect the many keys we need to encrypt all our data entities, we engage secure key stores, so called Hardware Security Modules (HSM). These are physical tamper-proof appliances that fulfill the purpose of protecting encryption keys from physical and cyber threats.
Our requirements for a secure key store
As encrypted data is only as secure as the key used for encryption, we have carefully chosen this core piece of security: A physical and digital vault to guard the keys to access our customers’ confidential data.
When choosing a key store we were looking for the following features:
Store keys safely and securely – the core functionality of any key store
As a place to store our thousands of keys safely.

Encryption services
Not to compromise any encryption keys, the keys are not allowed to leave the key store. So, we need encryption and decryption services that we can use from our application. As our business logic runs in a Java Virtual Machine (JVM), we require a JCA (Java Cryptography Architecture) integration.
Physical and cyber protection
A physical, tamper-proof appliance that resists mechanical manipulation to get physical access to the keys. Such appliances are called Hardware Security Modules (HSM).
All encryption services must provide access control using credentials to protect access from cyberspace.
Tenant support
For our white-labelling offer we wanted support for separated key spaces to separate data of different tenants full stack down to the key space.
Cluster support for failover and load balancing
With our highly dynamic data and keys we need a “live backup” of all keys currently in use. For this we want multiple synchronised key stores containing all keys at any time. By distributing the cluster members to different locations, we also get higher availability in any case of physical disturbance.
Key management
With that many keys we also need key creation services, which must assure every key’s quality. Also key deletion across the whole cluster is a daily operation and therefore a required service.
No auxiliary systems
Having auxiliary systems is always an extra operational effort and an additional security risk. Therefore, we require the key stores to be “self-contained” and to provide all the features, including cluster synchronization.
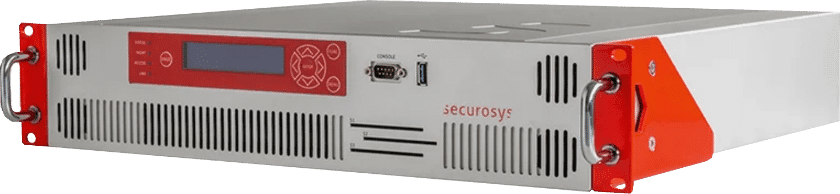
After careful evaluations we decided on the PRIMUS X HSM from Securosys. It is a tamper-proof physical appliance that fulfills Altoo’s requirements. Two Security Officer users are needed to configure the device. They are authenticated by personalised key cards, which enables us to enforce 4-eye principles for any device manipulation. The Primus HSM is built for multi-tenancy, which nicely maps to our requirements and allows us to separate tenants’ keys. Multiple PRIMUS X HSMs can be clustered without the need of additional auxiliary systems and are available in different performance classes to handle encryption load.
What Securosys says about their product:
“Securosys network attached Hardware Security Modules (HSMs) were developed for the Swiss financial sector. They have been designed and manufactured in Switzerland to meet the highest safety standards including physical security. The hardware is enclosed in shielded, tamper evident and resistant cases with a tamper proof key store. Our solutions are 100% trustworthy and can be audited by our customers. The modern architecture and components enable high performance and flexibility in terms of number of partitions and users.
The Primus Hardware Security Module (HSMs) performs a range of operations. It generates encryption keys, stores these keys, and manages the distribution of these keys. Besides key management, it can also perform authentication and encryption tasks. Multiple Primus HSMs can be grouped together as a cluster for redundancy and load balancing. Each Primus can also be partitioned for multiple users or applications.”
Altoo: Going the extra mile for security
In summary, we at Altoo use specialised security hardware to protect the access to our customers’ confidential wealth data. This is one of the many measures we take to maintain an outstanding level of information security – going the extra mile for security.
Further Readings:
- Our White Paper explains the Altoo Wealth Platform architecture.
- Our interactive website Security@Altoo provides an overview of our security measures including physical protection, cyber protection, and security measures within our business processes to ensure information security in the Altoo Wealth Platform.